Last Updated on November 16, 2019 by Mat Diekhake
WiFi has made connecting devices to the internet a much more manageable task to the lay’ than in days of earlier technology—no longer do you need to have a wire coming through your wall and attached to the side of your devices just so that you can use this thing called “the internet.”
WiFi is now almost everywhere: WiFi at home, WiFi when traveling—cars, buses, hotels, and even planes nowadays too—all offer WiFi connections to networks that’ll hook you up with the internet. What operating system you use will also determine what precise knowledge you need to have if you are to become a WiFi expert on your network. Some use WiFi on Mac, others WiFi on Windows or even Linux, all with different articles available to use for resources that you can find from the same search engines like Google.
If it weren’t for predetermined protection put in place, you’d be able to use the WiFi signals coming from your router anywhere within reasonable proximity. It’s the security put there by the technology, such as like WP2 (Wireless Protected Access—the second coming of) in current times, which mind you has been proven to be not as secure as people first thought, that allows us to restrict the WiFi usage to only the people we want. We do this by creating passwords, so you need to enter a password to start using the WiFi, and your neighbors relaxing inside their own homes or out in their yards would need to know that same password if there were to be able to connect to your internet. Pretty foolproof plan. . . .
But what if the unthinkable happens: what if someone has managed to work out your password and has used your data without your knowledge, purposefully using just enough for themselves to get by but not enough to the point they’ll think you notice. Or what if you have used your WiFi assuming that it is a secure network, but it actually isn’t, and other people around you didn’t even need to enter a password. Hell, they might even think you don’t mind them on your network with gifts such as these. . . . Making matters worse it isn’t just your data disappearing that you need to worry about either: if someone has managed to latch on to your WiFi network without your knowledge, then they could also be getting access to your files as well. Personal files, whatever you have coming from File Explorer and other devices attached to your computer.
Odder things have happened than both of the examples in the passage above, and you don’t need to be a technology prodigy to work out how to correct them all, because like with so many other things now in life, there are software programs out there to do all the arduous work for you. Some people don’t need to go to the trouble of installing software because their modern-day routers can expose a list of devices that are connected to it. In those circumstances, all you need to do is know the name of your device and anyone else’s that you’ve chosen to allow them to have WiFi access. Then any other unknown names are then likely to be unwanted. Nonetheless, not all routers have that feature and even if they do many people would have no idea how to go about finding the information. Those are the times you’ll want to check out what programs have to offer instead—and there are more than a few worth mentioning.
How to Check if Someone is Using Your Wireless Network with Wireless Network Watcher
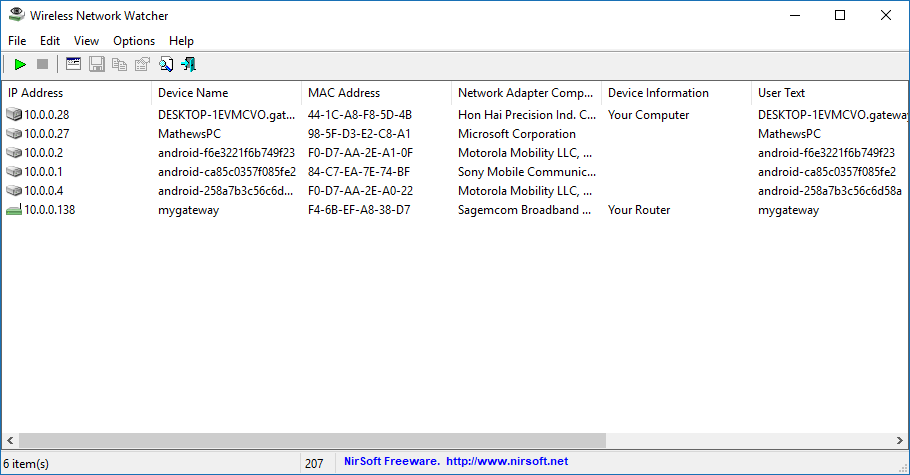
The Wireless Network Watcher is made by NirSoft, a company that has some very popular utilities that are being used by millions every month, and offers an easy, efficient and effective way to spot what devices are connected to your network quickly. After you’ve completed the setup it will scan your network and bring up the list of computers and mobile devices currently connected to your network. Each device will show the IP address, device name, Mac address, the manufacturer of the network card, and the computer name (when applicable).
Requirements:
- You can only use this utility if you have one of the following operating system versions: Windows 2000, Windows XP, Windows Server 2003, Windows Server 2008, Windows Vista, Windows 7, Windows 8, and Windows 10 (all editions).
- You can only use this utility to scan the wireless network that you are currently connected to—that’s referring to the computer you are also installing this problem on now.
- Although rare, it’s possible that the utility does not detect the correct wireless network at times. If that happens, you need to go to the advanced options by pressing the “F9” key on your keyboard and then manually choose the correct network adapter name yourself from the list.
How to Set Up Wireless Network Watcher
Visit the Wireless Network Watcher utility webpage, scroll down and then click on the “Download Wireless Network Watcher with full install/uninstall support (wnetwatcher_setup.exe)” link. It’ll then download the file above the taskbar of your computer. Wait for it to finish, click on the file and then you’ll see the beginning of the setup wizard just like in the example below. Click on the “Next” button when you get to it.
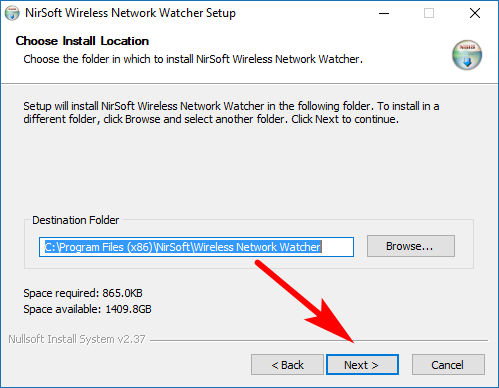
Choose where on the computer you would like to store the file by clicking on the “Browse” button next to where it says the “Destination folder” or just leave it on the default location if you don’t have any preference Click on the “Next” button to continue.
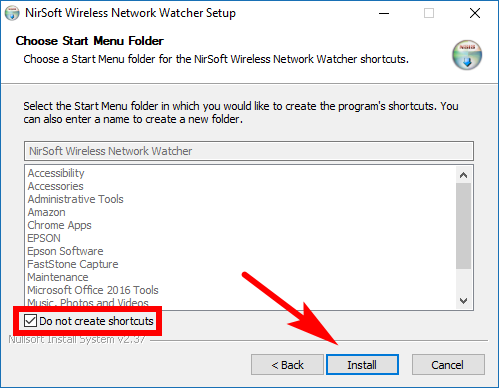
Since lots of people want to keep this software installed on the computer over time, the program lets you choose a location in the Start menu if you want a shortcut. If you don’t want one, just check the “Do not create shortcuts” box outlined in the example below. Click on the “Install” button when you’re ready to install the Wireless Network Watcher program.
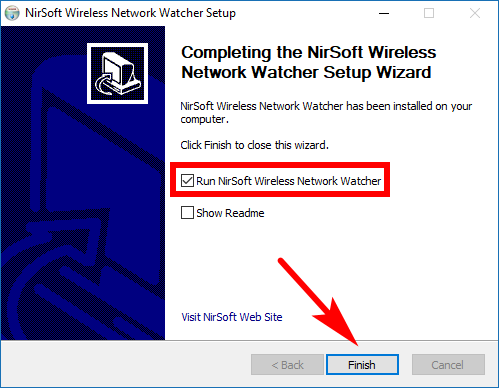
Keep the run box checked and then click on the “Finish” button, the setup wizard then closes, and you get to see your installed program in action.
Give it a few seconds to finish populating and then you’ll see the list of devices currently connected to your network. The UI will vary slightly depending on what versions of the Windows operating system you are using—the example below is done on Windows 10.
How to Check if Someone is Using Your Wireless Network with SoftPerfect WiFi Guard
WiFi Guard is a more specialized network scanner to SoftPerfect’s other beautifully developed SoftPerfect Network Scanner tool. Lots of people use WiFi Guard to prevent problems with vulnerabilities in encryption and brute force attacks, even if your networks are usually well protected. Once installed it pings each computer and mobile device connected to the network and shows them all from its user interface live. It comes with a Windows installer and portable version. Other operating system users such as Mac and Linux get to use this tool as well.
How to Set Up WiFi Guard
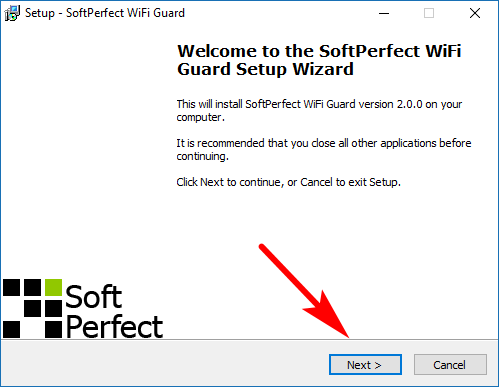
Visit the SoftPerfect downloads webpage and look for your operating system in the left side pane. Click on the link that matches your OS, and it’ll begin to download to your computer. Click on the file once it’s finished downloading and then you’ll open up what is the beginning of the setup wizard. Click on the “Next” button at the bottom of the front page.
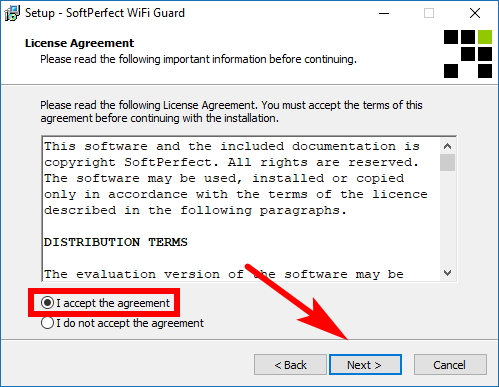
Like most software, there are terms you need to agree to before they’ll allow it to be installed on your computer. Have a read of them if you want to potentially cancel the installation, but if you want to continue, you have no choice but to accept them. Click on the checkbox available next to where it says “I accept the agreement” and then click on the “Next button.
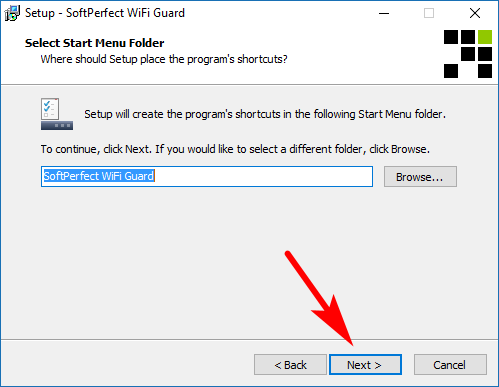
Click on the “Browse” button if you would like to choose a different location in the Start menu (if you installed the Windows version) or just leave it on the default setting and click on the “Next” button to continue.
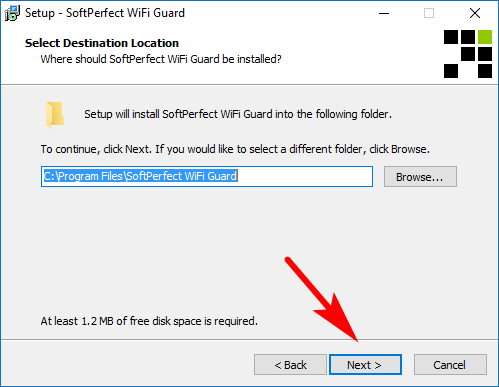
Click on the “Browse” button if you would like to change the storage location (where the file will be stored) or just click on the “Next” button if you’re happy with the defaults and ready continue.
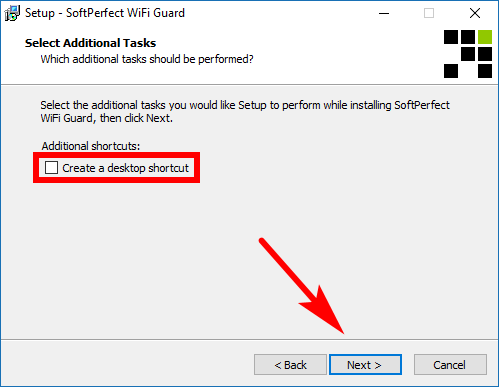
It then gives you the option of creating a desktop shortcut if you want it, otherwise just click on the “Next” button once again at the bottom of the window.
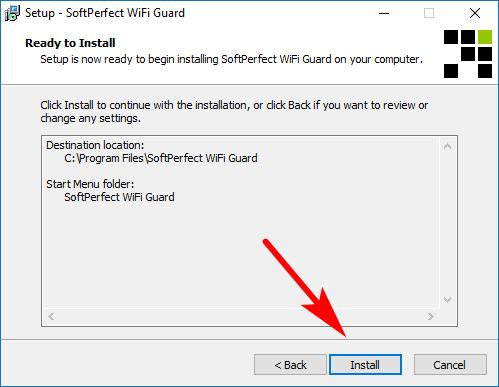
Your program is now ready to install. Click on the “Install” button and then give it a few seconds to complete its installation.
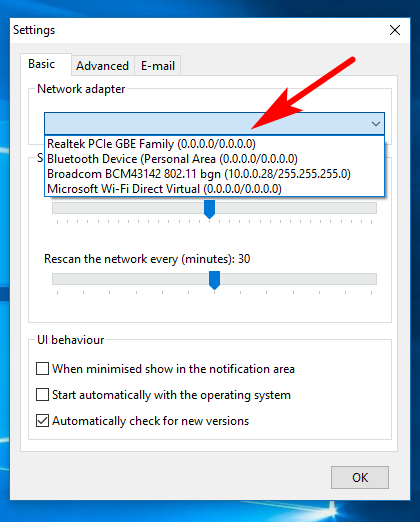
The first thing you’ll see when you open it up is the Settings dialog box. You have to click on the “Network adapter” drop-down menu and choose your network before it can work. Do that on your own settings and then click on the “OK” button at the bottom of the window.
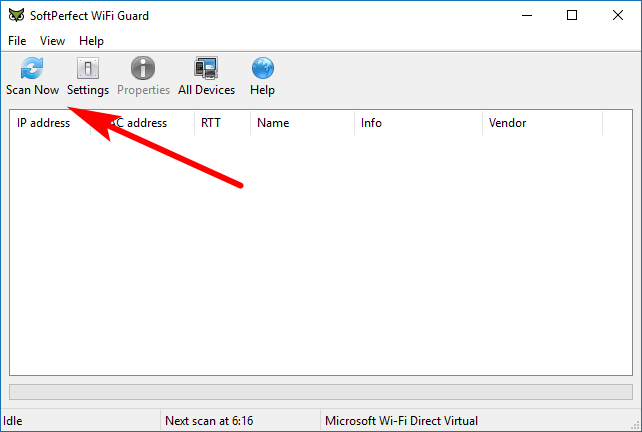
You then get your SoftPerfect WiFi Guard user interface. Click on the “Scan now” button to scan for the networks.
You can also click on the “File” menu and then “All Devices” to see all your devices that are connected to the network.
The Wireless Network Watcher and WiFi Guard software are probably leading the way, from what we can gather, but there are some more alternatives if you still want more. Another popular choice is the Advanced IP Scanner, that is a network administration tool, and one of the features you get with it is the chance to scan networks for connections. Angry IP Scanner is very similar again and has the option of scanning your network connections from the three main operating systems used today, including Mac and Linux. Appropriately named Who Is On My WiFi is a tool that solely focuses on scanning your network connections, although the free version only lets you see who is on the connection and not remove them. To block unknown or unidentified connections requires the paid version instead.
You don’t need to be a computer wizard to check out who is connecting to your network connections these days thanks to software out there that is willing to help you out after you install it. All of these tools have been checked for any junkware, and they’re all clean. Some of the sites are more popular than others, but some of them also host a range of tools and not just a few, so just assessing the tools based on the traffic they are getting isn’t easy to do. Nevertheless, every tool on this list comes up as safe and are tools we would recommend giving a go if you ever think someone else might be connecting to your WiFi to use your data or check out your files.
You might also be interested in:
- How to Rename URL for Favorites in Microsoft Edge in Windows 10
- How to Boot to Advanced Startup Options in Windows 10
- How to Undo a System Restore in Windows 10
- How to Change Number of Times Windows 10 Creates Restore Points
You can subscribe to our RSS, follow us on Twitter or like our Facebook page to keep on consuming more tech.